A test of encapsulation security in C#
I am taking a Computer Security course as part of my Masters of Computer Science and a specific question inspired the idea of testing the security of Encapsulation in C#.
I was curious, if exposing an object that is not exposed would be as simple as changing a single bit with a hex editor.
So I created two projects:
A dll that doesn’t expose two objects.
namespace EncapsulatedLibrary
{
class Class1
{
public int i = 27;
}
class Class2
{
public int i = 29;
}
}
An executable that references the dll and tries to use objects that are not exposed.
using EncapsulatedLibrary;
namespace TestLink
{
class TestLinkProgram
{
static void Main(string[] args)
{
Class1 c1 = new Class1();
int val1 = c1.i;
Class2 c2 = new Class2();
int val2 = c2.i;
}
}
}
Ok, now if you compile these, the dll compiles fine, but the exe fails to build.
Now try to use a hex editor to change the compiled version of the dll to expose these objects.
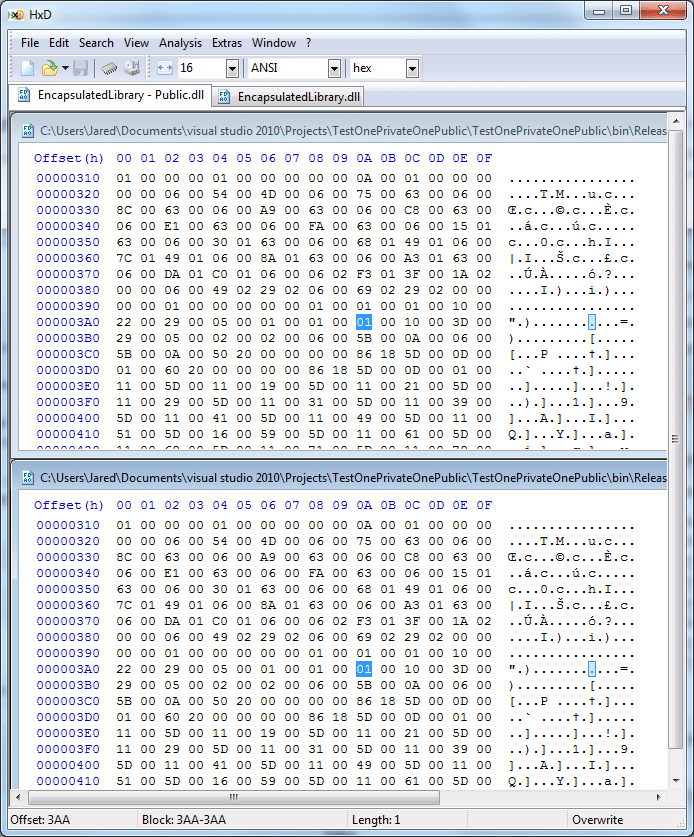
So real quick, I copied the dll and then changed the classes to public and recompiled. Then using a hex editor, HxD, I compared the two files.
Sure enough, on row 00000390, the 13th octet, I changed it from 00 to 01 and now Class1 is public.
On the very next row, 000003A0, the 10th octet, I changed it from 00 to 01 and now Class2 is public.
With this simple hack, I have made two objects public that should not be public. While in this example, this is not malicious, there are ways this could be used maliciously. Imagine if you had functionality limitations on users and they should not have rights to do certain processes but due to exposing a library, they can do these processes.
So now the next question left to be answered is this: What tools exist as controls to prevent such an attack?


Silly security response: the user owns the computer, and thus, you can't protect a program from being modified. Because even if you try to detect such a change, the user can nop out that code too, and in the end, you can't secure it.
The longer answer is that tools existed in the DOS days to do a CRC on an EXE, and then a CRC check was done at run time to make sure the program hadn't been modified. Similar things exist for newer languages. Email me if you want a working version for C#.